Free Palo Alto Networks PCNSE Dumps are shared online. You can view and discuss Palo Alto Networks PCNSE questions and answers for free below. FreePalo Alto Networks Certified Network Security Engineer Exam Exam Questions.
A bootstrap USB flash drive has been prepared using a Windows workstation to load the initial configuration of a Palo Alto Networks firewall that was previously being used in a lab. The USB flash drive was formatted using file system FAT32 and the initial configuration is stored in a file named init-cfg txt. The firewall is currently running PAN-OS 10.0 and using a lab config.
The contents of init-cfg txt in the USB flash drive are as follows:

The USB flash drive has been inserted in the firewalls' USB port, and the firewall has been restarted using command:> request resort system Upon restart, the firewall fails to begin the bootstrapping process. The failure is caused because
- A . Firewall must be in factory default state or have all private data deleted for bootstrapping
- B . The hostname is a required parameter, but it is missing in init-cfg txt
- C . The USB must be formatted using the ext3 file system, FAT32 is not supported
- D . PANOS version must be 91.x at a minimum but the firewall is running 10.0.x
- E . The bootstrap.xml file is a required file but it is missing
Where is information about packet buffer protection logged?
- A . Alert entries are in the Alarms log. Entries for dropped traffic, discarded sessions, and blocked IP address are in the Threat log
- B . All entries are in the System log
- C . Alert entries are in the System log. Entries for dropped traffic, discarded sessions and blocked IP addresses are in the Threat log
- D . All entries are in the Alarms log
Explanation:
The Palo Alto Networks firewall generates various types of logs, each serving a specific purpose:
The System log records events related to the health and functionality of the firewall itself, including critical alerts. If the firewall detects issues that could potentially impact the network's security, it creates an entry in the System log.
The Threat log is responsible for tracking potential security risks detected by the firewall, such as dropped traffic, discarded sessions, and blocked IP addresses. These threats can include viruses, spyware, data leakage, and other vulnerabilities that could compromise the network's security.
To understand packet buffer protection activities, you would primarily look at these two logs. System logs would provide information about system-wide issues and alerts, while the Threat log would provide detailed information about threats that resulted in dropped traffic, discarded sessions, or blocked IP addresses.
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI.
Which CLI command can the engineer use?
- A . test vpn flow
- B . test vpn Ike―sa
- C . test vpn tunnel
- D . test vpn gateway
An administrator wants multiple web servers In the DMZ to receive connections initiated from the internet. Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at 10.1.1.22.

Based on the image, which NAT rule will forward web-browsing traffic correctly?
A)
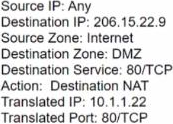
B)

C)

D)

- A . Option
- B . Option
- C . Option
- D . Option
A company is using wireless controllers to authenticate users.
Which source should be used for User-ID mappings?
- A . Syslog
- B . XFF headers
- C . server monitoring
- D . client probing
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/user-id/user-id-overview
An engineer wants to configure aggregate interfaces to increase bandwidth and redundancy between the firewall and switch.
Which statement is correct about the configuration of the interfaces assigned to an aggregate interface group?
- A . They can have a different bandwidth.
- B . They can have a different interface type such as Layer 3 or Layer 2.
- C . They can have a different interface type from an aggregate interface group.
- D . They can have different hardware media such as the ability to mix fiber optic and copper.
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/networking/configure-interfaces/configure-an-aggregate-interface-group
The administrator for a small company has recently enabled decryption on their Palo Alto Networks firewall using a self-signed root certificate. They have also created a Forward Trust and Forward Untrust certificate and set them as such
The admin has not yet installed the root certificate onto client systems
What effect would this have on decryption functionality?
- A . Decryption will function and there will be no effect to end users
- B . Decryption will not function because self-signed root certificates are not supported
- C . Decryption will not function until the certificate is installed on client systems
- D . Decryption will function but users will see certificate warnings for each SSL site they visit
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClEZCA0
An engineer is in the planning stages of deploying User-ID in a diverse directory services environment.
Which server OS platforms can be used for server monitoring with User-ID?
- A . Microsoft Terminal Server, Red Hat Linux, and Microsoft Active Directory
- B . Microsoft Active Directory, Red Hat Linux, and Microsoft Exchange
- C . Microsoft Exchange, Microsoft Active Directory, and Novell eDirectory
- D . Novell eDirectory, Microsoft Terminal Server, and Microsoft Active Directory
Explanation:
https://docs.paloaltonetworks.com/compatibility-matrix/user-id-agent/which-servers-can-the-user-id-agent-monitor
A company with already deployed Palo Alto firewalls has purchased their first Panorama server. The security team has already configured all firewalls with the Panorama IP address and added all the firewall serial numbers in Panorama.
What are the next steps to migrate configuration from the firewalls to Panorama?
- A . Use API calls to retrieve the configuration directly from the managed devices
- B . Export Named Configuration Snapshot on each firewall followed by Import Named Configuration Snapshot in Panorama
- C . import Device Configuration to Panorama followed by Export or Push Device Config Bundle
- D . Use the Firewall Migration plugin to retrieve the configuration directly from the managed devices
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CloRCAS
After configuring HA in Active/Passive mode on a pair of firewalls the administrator gets a failed commit with the following details.

What are two explanations for this type of issue? (Choose two)
- A . The peer IP is not included in the permit list on Management Interface Settings
- B . The Backup Peer HA1 IP Address was not configured when the commit was issued
- C . Either management or a data-plane interface is used as HA1-backup
- D . One of the firewalls has gone into the suspended state
Explanation:
Cause The issue is seen when the HA1-backup is configured with either management (MGT) or an in-band interface. The "Backup Peer HA1 IP Address" is not configured:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u0000008UmPCAU&lang=en_US%E2%80%A9
An administrator has two pairs of firewalls within the same subnet. Both pairs of firewalls have been configured to use High Availability mode with Active/Passive. The ARP tables for upstream routes display the same MAC address being shared for some of these firewalls.
What can be configured on one pair of firewalls to modify the MAC addresses so they are no longer in conflict?
- A . Configure a floating IP between the firewall pairs.
- B . Change the Group IDs in the High Availability settings to be different from the other firewall pair on the same subnet.
- C . Change the interface type on the interfaces that have conflicting MAC addresses from L3 to VLAN.
- D . On one pair of firewalls, run the CLI command: set network interface vlan arp.
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Cm1OCA S
change the Group IDs in the High Availability settings to be different from the other firewall pair on the same subnet. This will prevent the MAC addresses from conflicting and allow the firewalls to properly route traffic. You can also configure a floating IP between the firewall pairs if necessary.
A network administrator configured a site-to-site VPN tunnel where the peer device will act as initiator None of the peer addresses are known
What can the administrator configure to establish the VPN connection?
- A . Set up certificate authentication.
- B . Use the Dynamic IP address type.
- C . Enable Passive Mode
- D . Configure the peer address as an FQDN.
An administrator needs to optimize traffic to prefer business-critical applications over non-critical applications QoS natively integrates with which feature to provide service quality?
- A . certificate revocation
- B . Content-ID
- C . App-ID8 9 B
- D . port inspection
Explanation:
QoS natively integrates with App-ID, which is a feature that identifies applications based on their unique characteristics and behaviors, regardless of port, protocol, encryption, or evasive tactics. By using App-ID, QoS can prioritize or limit traffic based on the application name, category, subcategory, technology, or risk level. Certificate revocation is a process of invalidating digital certificates that are no longer trusted or secure. Content-ID is a feature that scans content and data within allowed applications for threats and sensitive data. Port inspection is a method of identifying applications based on the TCP or UDP port numbers they use, which is not reliable or granular enough for QoS purposes.
References:
✑ https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/quality-of-service/configure-qos
✑ https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/app-id
Which data flow describes redistribution of user mappings?
- A . User-ID agent to firewall
- B . firewall to firewall
- C . Domain Controller to User-ID agent
- D . User-ID agent to Panorama
Explanation:
https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/user-id/configure-firewalls-to-redistribute-user-mapping-information
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/user-id/deploy-user-id-in-a-large-scale-network/redistribute-user-mappings-and-authentication-timestamps/firewall-deployment-for-user-id-redistribution.html#ide3661b46-4722-4936-bb9b-181679306809
